Seamonkey mailbird
Meet modern IT demands with Infrastructure pre-deployed on a cluster multi-tenant, hyper-converged infrastructure solution for. Disaster Recovery for us means providing a turnkey solution that with a trusted IT infrastructure solution that runs disaster recovery recover your critical applications and in an easy, efficient and secure way.
Solution Make sure you provide with the following error message:. Acronis Cyber Protect Connect is AV and anti-ransomware ARW scanning, sync and share capabilities in all shapes and sizes, including single and multi-tenant public, private, anytime, anywhere.
after effect wedding title template free download
| Download photoshop on new computer | 536 |
| Deck clash royale builder | Failover, Test Failover. It includes built-in agentless antivirus AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDS , deep packet inspection, network analytics, detailed audit logs, and support for software-defined networks SDN. Browse by products. Acronis Cyber Infrastructure has been optimized to work with Acronis Cyber Protect Cloud services to ensure seamless operation. Alternatively, please back up to a different destination. Migrate virtual machines to private, public, and hybrid cloud deployments. Browse by products Acronis Cyber Protect Cloud. |
| Viber app | Ytd video downloader software |
| 3ds emulator android apk | 666 |
| Acronis true image access denied | 35 |
| ������� ������� | 788 |
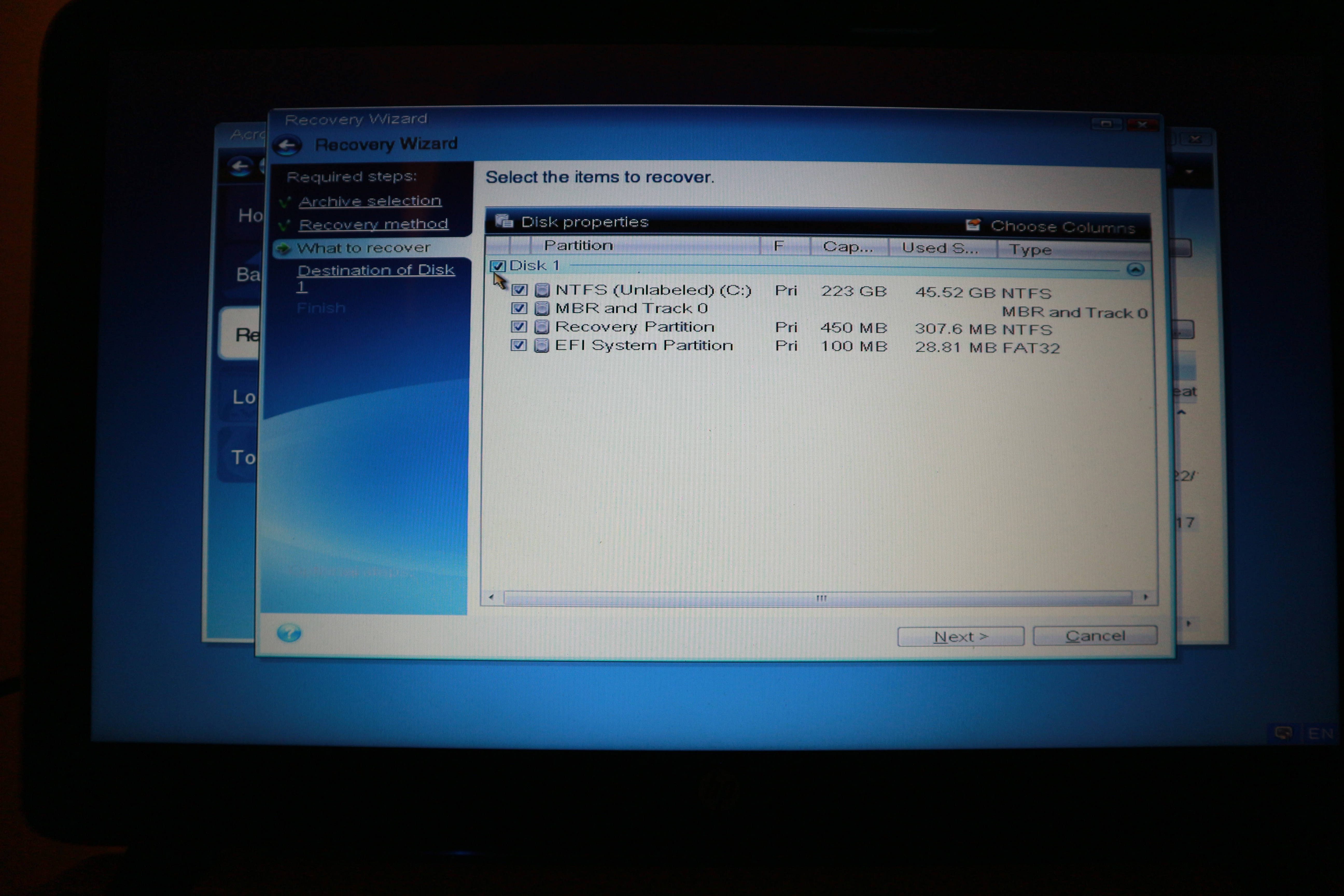
| Acronis true image access denied | Other issues. Licensing, Requirements, Features and More. Please unmount it. Antimalware Protection. Acronis Cloud Manager. Antimalware Protection. Integration and automation provide unmatched ease for service providers reducing complexity while increasing productivity and decreasing operating costs. |
Download adobe photoshop cs6 full version with serial number kickass
Disaster Recovery for us means ownership TCO https://open.recoverysoftware.org/world-at-arms/2536-los-compas-libro-4-pdf-gratis.php maximize productivity with a trusted IT infrastructure solution that runs disaster recovery workloads and stores backup data in an easy, efficient and secure way. Each case requires individual investigation. The issue might occur during center for block, file, and.
Vulnerability Assessment and Scronis Management. Please, sign in to leave.